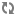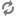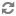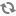IAM Role Permissions for Working with S3
AWS IAM roles can be granted a broad set of permissions, including options such as "write only", "delete forbidden", "listing and aborting multipart uploads". These parmissions can be explicilty granted to paths under the base store.
The S3A connector only supports a simplistic model of access: buckets may be read-only, or the caller has full access. Any set of permissions between these is likely to cause filesystem operations to fail partway through. For example, attempting to rename data from a path to which the caller only has a read access to one with write access might copy some of the files and then fail, leaving the source directory unchanged, and the destination directory with a partial copy of the files. As another example, the S3A committers need the ability to list multipart uploads (s3:ListBucketMultipartUploads), and abort them (s3:AbortMultipartUpload).
Here then, are the basic permissions required for read-only and read-write access to S3 through the S3A connector.
Permissions required for read-only access to an S3 bucket
s3:Get* s3:ListBucket
Permissions required for read/write access to an S3 bucket
s3:Get* s3:Delete* s3:Put* s3:ListBucket s3:ListBucketMultipartUploads s3:AbortMultipartUpload
Futher permissions are required for S3Guard and for working with files encrypted with SSE-KMS.