Setting up Knox SSO for Ranger
This section describes how to configure Ranger to use Knox SSO (Single Sign-on) to authenticate users on an Ambari cluster. With this configuration, unauthenticated users who try to access Ranger are redirected to the Knox SSO login page for authentication.
![[Note]](../common/images/admon/note.png) | Note |
|---|---|
|
Use the following steps to configure Knox SSO for Ranger:
Install Ambari with HDP-2.5 or higher. Install Knox along with the other services.
The Knox SSO topology settings are preconfigured in Knox > Configs > Advanced knoxsso-topology.
Run the following CLI command to export the Knox certificate:
JAVA_HOME/bin/keytool -export -alias gateway-identity -rfc -file <cert.pem> -keystore /usr/hdp/current/knox-server/data/security/keystores/gateway.jks
When prompted, enter the Knox master password.
Note the location where you save the
cert.pemfile.
Select Ranger > Configs > Advanced > Knox SSO Settings and set the following properties:
Enable Ranger SSO – Select this check box to enable Ranger SSO.
SSO provider url –
https://<knox_host>:8443/gateway/knoxsso/api/v1/webssoSSO public key – Paste in the contents of the
cert.pemcertificate file exported from Knox.When you paste the contents, exclude the header and footer.
SSO browser useragent – Preconfigured with
Mozilla,chrome.
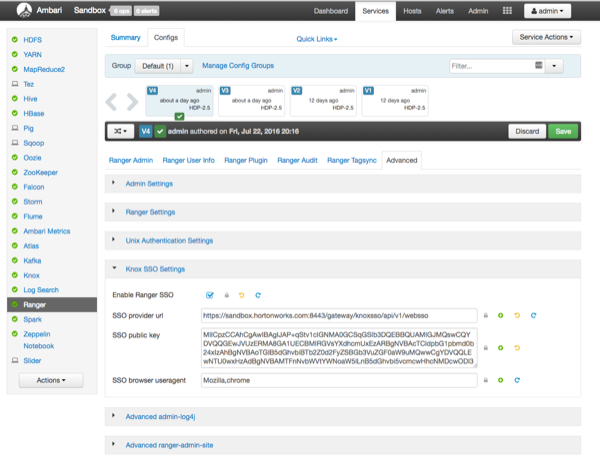
[D]Click Save to save the new configuration, then click through the confirmation pop-ups.
Restart Ranger. Select Actions > Restart All Required to restart all other services that require a restart.
Knox SSO should now be enabled. Users who try to access Ranger are redirected to the Knox SSO login page for authentication.