Configuring Atlas Authorization
You can use Apache Atlas authorization to restrict access to Apache Atlas.
More specifically, you can restrict access to Atlas types and entities, and to administrative operations.
Access to Types
- Create
- Update
- Delete
Access to Entities
- Read
- Create
- Update
- Delete
- Add classification
- Update classification
- Remove classification
Admin Operations
- admin-export
- admin-import
You can use simple or Ranger authorization:
- Simple authorization – Authorization policies are specified using a JSON file.
- Ranger authorization – Authorization policies are specified using Apache Ranger.
Configure Simple Authorization
- Select Atlas > Configs > Advanced on the Ambari dashboard, then click Advanced application-properties.
- Set the value of the
atlas.authorizer.implproperty tosimple. - Confirm that the value of the
atlas.simple.authz.policy.fileproperty is set to{{conf_dir}}/atlas-simple-authz-policy.json. - Edit the
{{conf_dir}}/atlas-simple-authz-policy.jsonfile to specify authorization settings:vi /usr/hdp/current/atlas-server/conf/atlas-simple-authz-policy.jsonThe following is a sample
atlas-simple-authz-policy.jsonfile:{ "roles": { "ROLE_ADMIN": { "adminPermissions": [ { "privileges": [ ".*" ] } ], "entityPermissions": [ { "privileges": [ ".*" ], "entityTypes": [ ".*" ], "entityIds": [ ".*" ], "classifications": [ ".*" ] } ], "typePermissions": [ { "privileges": [ ".*" ], "typeCategories": [ ".*" ], "typeNames": [ ".*" ] } ] }, "DATA_SCIENTIST": { "entityPermissions": [ { "privileges": [ "entity-read"], "entityTypes": [ ".*" ], "entityIds": [ ".*" ], "classifications": [ ".*" ] } ] }, "DATA_STEWARD": { "entityPermissions": [ { "privileges": [ "entity-read", "entity-create", "entity-update", "entity-add-classification", "entity-update-classification", "entity-remove-classification" ], "entityTypes": [ ".*" ], "entityIds": [ ".*" ], "classifications": [ ".*" ] } ] } }, "userRoles": { "admin": [ "ROLE_ADMIN" ] }, "groupRoles": { "ROLE_ADMIN": [ "ROLE_ADMIN" ], "hadoop": [ "DATA_STEWARD" ], "DATA_STEWARD": [ "DATA_STEWARD" ], "RANGER_TAG_SYNC": [ "DATA_SCIENTIST" ] } } - To apply these permissions, restart Atlas and any other services that require a restart.
Configure Ranger Authorization
- On the Ranger Configs page, select the Ranger Plugin tab.
- Under Atlas Ranger Plugin, select On, then click Save in the black menu
bar.
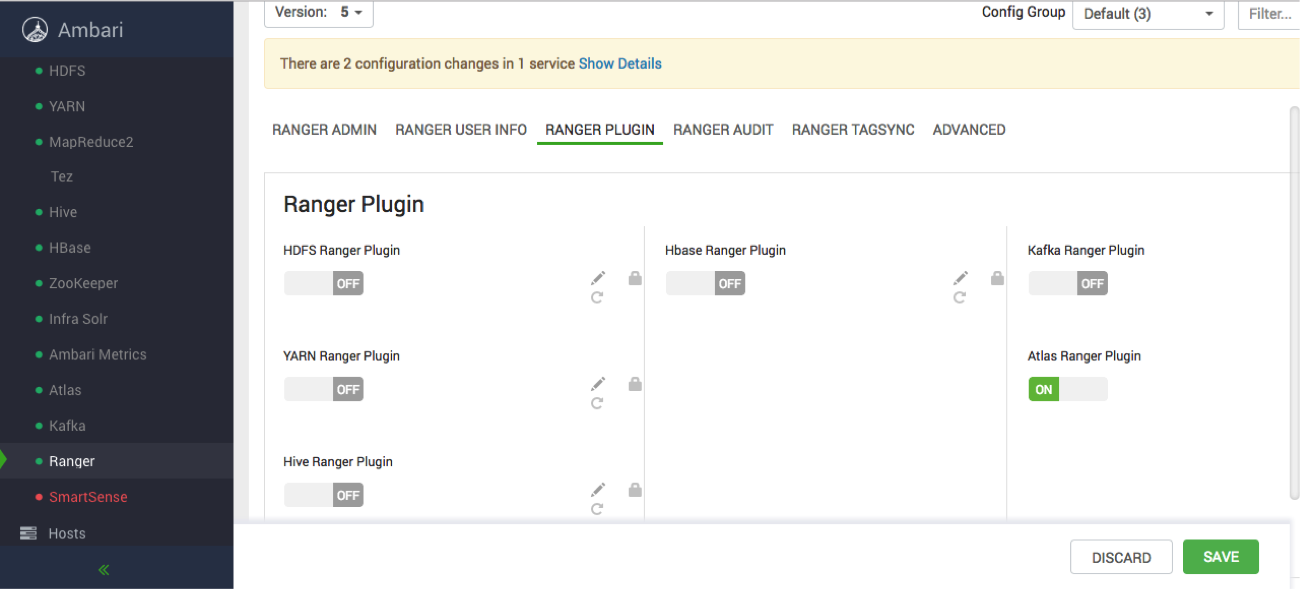
- A Save Configuration pop-up appears. Type in a note describing the changes you just made, then click Save.
- A Dependent Configurations pop-up appears. Click OK to confirm the recommended
configuration updates.
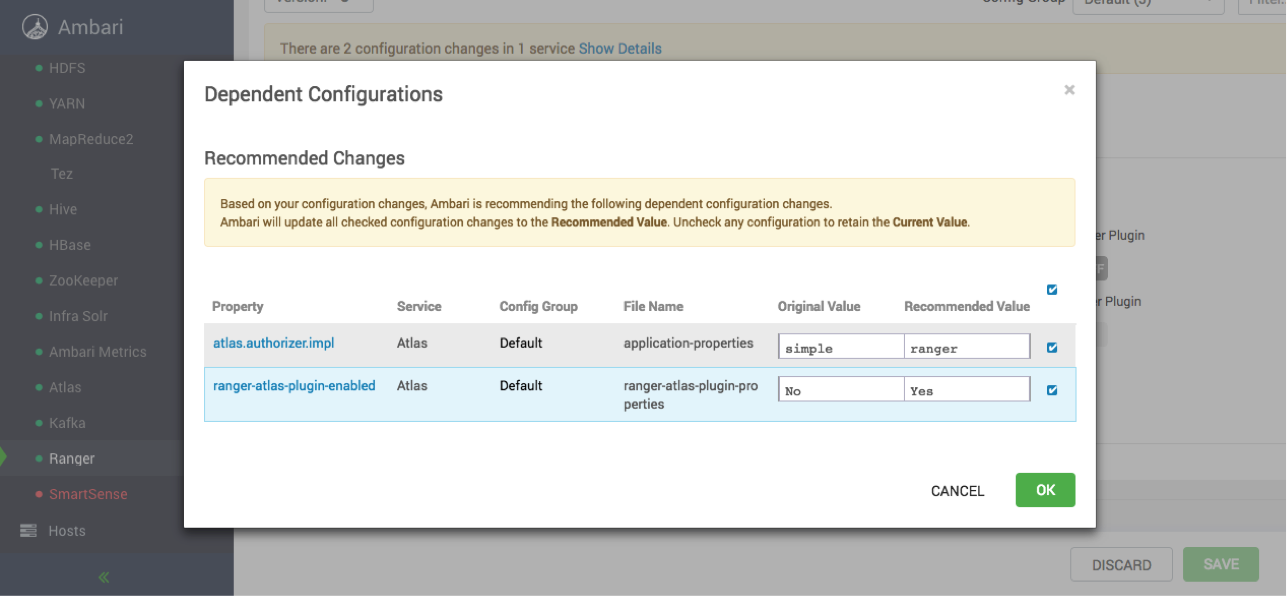
- Click OK on the Save Configuration Changes pop-up.
- Select Actions in the navigation menu, then select Restart All Required to restart all services that require a restart.
- Click Confirm Restart All on the confirmation pop-up to confirm the Storm restart. After the services restart, the Ranger plugin for Atlas is enabled.
- Log in to the Apache Ranger Web UI.
- On the Apache Ranger Service Manager page, select an existing service under Atlas.
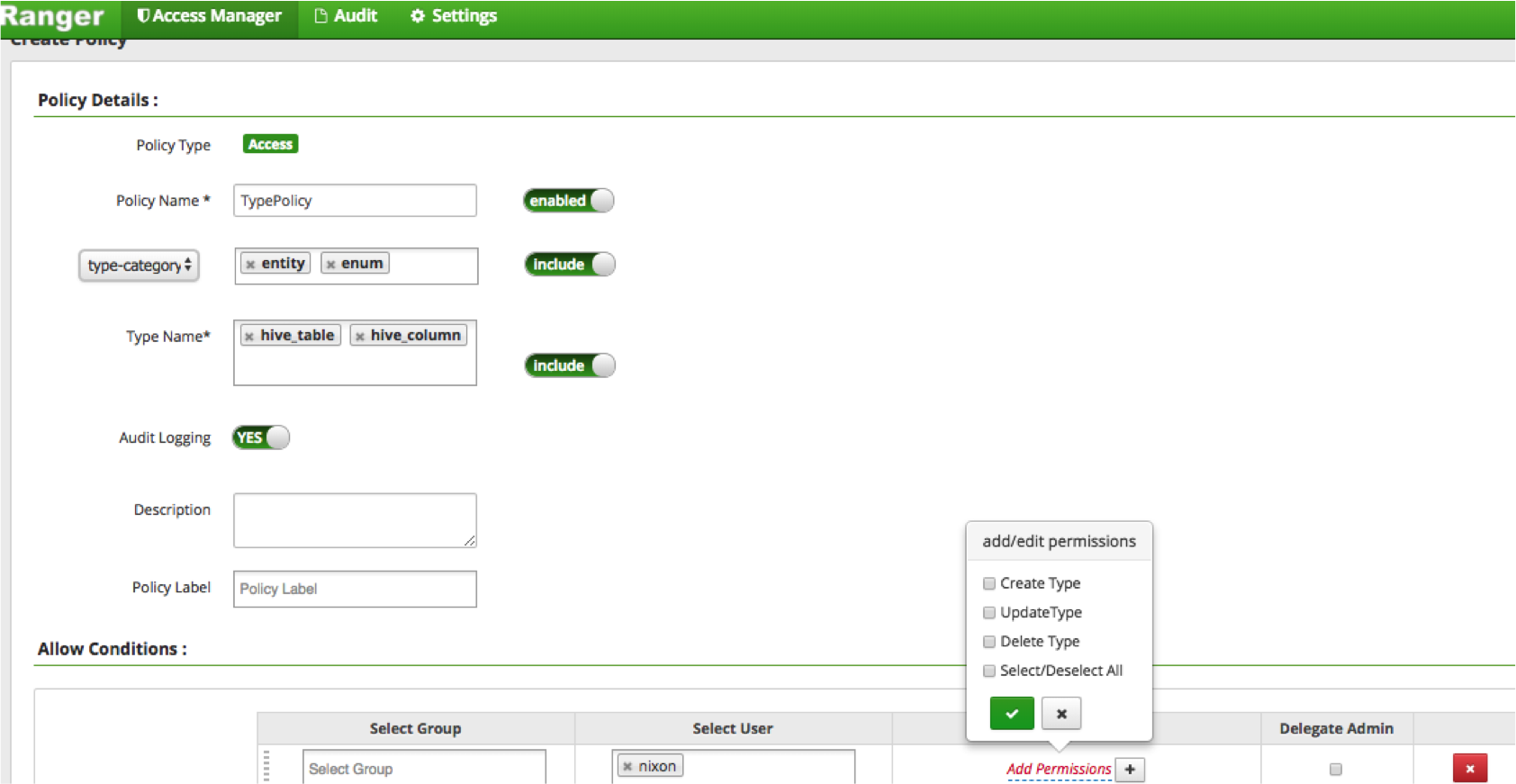
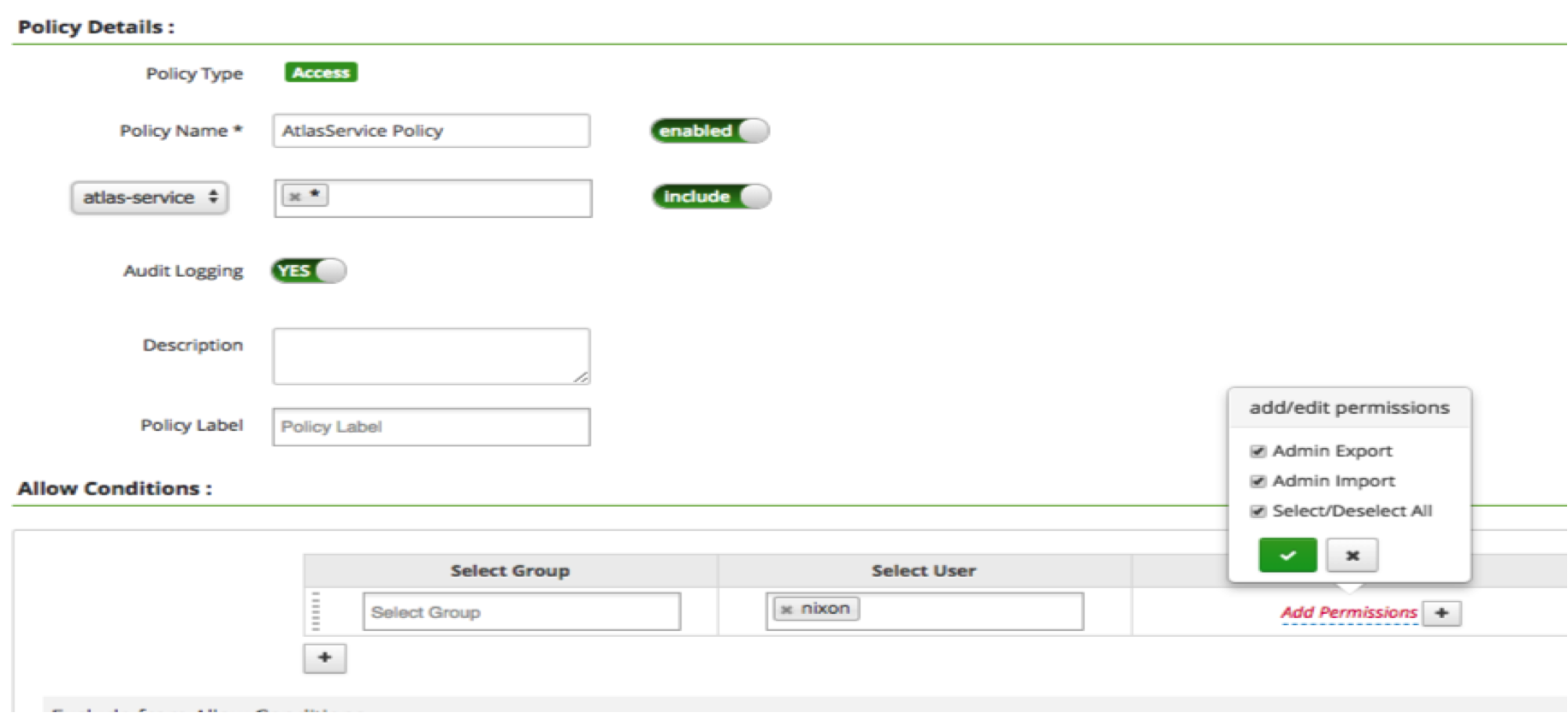
- On the List of Policies page, click Add New Policy.
- Use the Create Policy page to specify the Atlas authorization policy, then click
Add. The following figures show sample Ranger policy pages for Atlas
authorization.
Authorize Access to Atlas Types
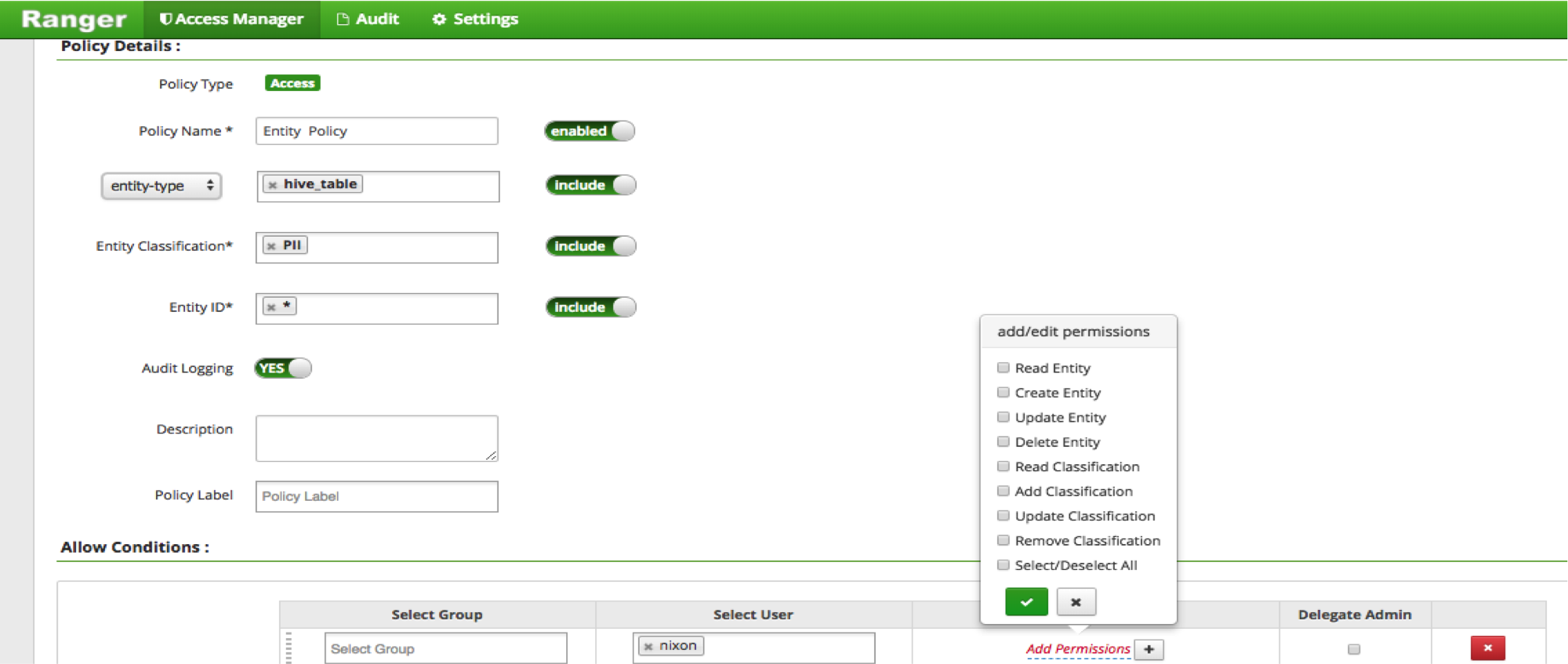
Authorize Access to Atlas Entities
Authorize Access to Atlas Admin Operations
Authorization in the Apache Atlas Web UI
An error message appears in the Atlas Web UI if a user attempts to perform an unauthorized operation.
You should also note that Atlas Search displays all results, but if a user does not have Read permissions for some of the search results, links will not be available to access those entities.

