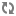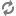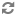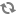Configuring Encryption for Specific Buckets
S3A's per-bucket configuration mechanism can be used to configure the encryption
mechanism and credentials for specific buckets. For example, to access the bucket called
"production" using SSE-KMS with the key ID
arn:aws:kms:us-west-2:360379543683:key/071a86ff-8881-4ba0-9230-95af6d01ca01,
the settings are:
<property> <name>fs.s3a.bucket.production.server-side-encryption-algorithm</name> <value>SSE-KMS</value> </property> <property> <name>fs.s3a.bucket.production.server-side-encryption.key</name> <value>arn:aws:kms:us-west-2:360379543683:key/071a86ff-8881-4ba0-9230-95af6d01ca01</value> </property>
Per-bucket configuration does not apply to secrets kept in JCEKS files; the core
configuration properties must be used (for example
fs.s3a.server-side-encryption.key), with the path to the JCEKS file instead
configured for the bucket:
<property> <name>fs.s3a.bucket.production.server-side-encryption-algorithm</name> <value>SSE-KMS</value> </property> <property>` <name>fs.s3a.bucket.production.security.credential.provider.path</name> <value>hdfs://common/production.jceks</value> </property>
To learn more, refer to Protecting Data Using Server-Side Encryption with Customer-Provided Encryption Keys (SSE-C) in AWS documentation.