Using the PCAP Panel UI to Query pcap Data
The PCAP panel user interface is ideally suited for the SOC analyst who is identifying and investigating malicious events. You can use the PCAP panel to refine query information provided by other UIs such as the Alerts or Kibana tools. The PCAP panel uses the fixed filter option to query the PCAP data. The PCAP panel provides a graphical user interface to explicitly define the parameters used in the query.
- Display the Ambari user interface.
- If you have not already done so, in the Services pane, select Metron.
- From the Quick Links menu, choose Alerts UI.
- From the Alerts UI, click the PCAP tab.
-
Use the date, IP information, and protocol fields to define the parameters of your
query, then click
 (search icon).
(search icon).
 NoteOnly one job can be run at a time.You can stop a job by clicking the X next to the job progress bar.
NoteOnly one job can be run at a time.You can stop a job by clicking the X next to the job progress bar.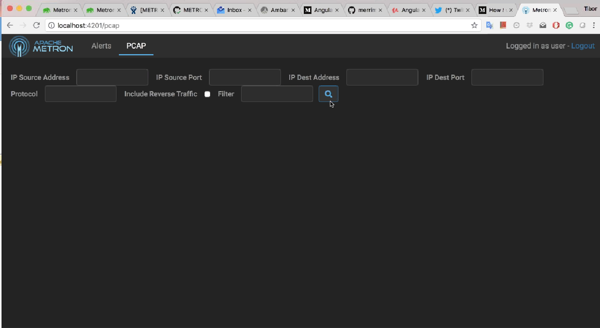
 NoteThe response time of a query is dependent on the precision of your search parameters. If your search parameters are too broad, the query could take a long time and provide results that are too imprecise to be helpful.
NoteThe response time of a query is dependent on the precision of your search parameters. If your search parameters are too broad, the query could take a long time and provide results that are too imprecise to be helpful.- From and To
- The starting and end dates of your search.
- The From field defaults to 5 days prior to current date. The To field defaults to the current date and time.
- IP Source Address
- The IP source address.
- IP Source Port
- The IP source port.
- IP Dest Address
- The IP destination address.
- IP Dest Port
- The IP destination port.
- Protocol
- The network protocol. This should be the string value of the protocol.
- Include Reverse Traffic
- Queries bi-directionally. Runs the query so that it swaps the order of the query between IP Source address and Destination Address.
- Filter
- Allows you to run a binary regular expression.
- Filtering can be done both by the packet header as well as with a binary
regular expression which can be run on the packet payload itself. This
filter can be specified with:
- The
-pfor--packet_filteroptions for the fixed query filter - The
BYTEARRAY_MATCHER(pattern, data)Stellar function. The first argument is the regex pattern and the second argument is the data. The packet data will be exposed by thepacketvariable in Stellar.
- The
- To download the PCAP filter data, click Download PCAP, then specify where to save the data.

