Using Zeppelin to Analyze Data
Zeppelin enables you to analyze the enriched telemetry information Metron archives in HDFS.
The following example guides you through using Zeppelin to perform different types of analyses on the Bro telemetry information to discover a potential issue.
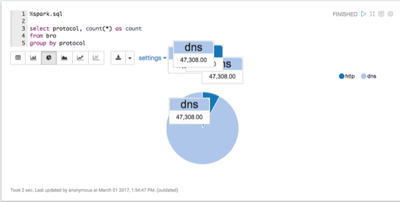
Bro produces data about a number of different network protocols. View which types of protocols exist in the data.
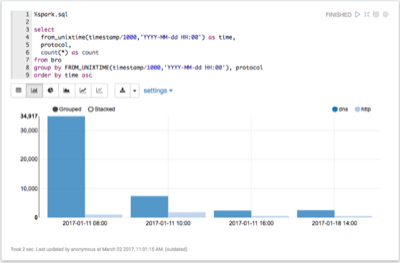
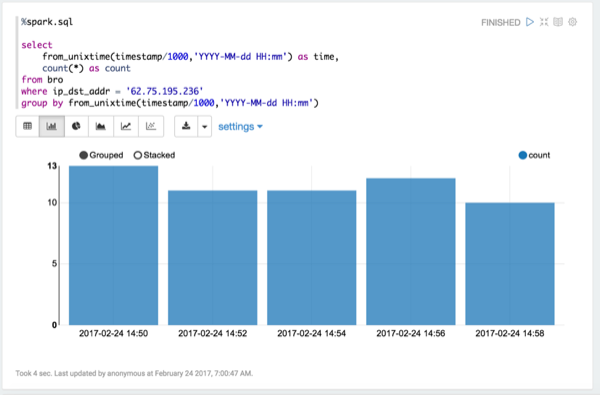
View when Bro telemetry information was received.
You can check for any odd gaps and fluctuating periods of high and low activity.
![[Note]](../common/images/admon/note.png)
Note If there is not enough data for this visualization to be interesting, let Metron consume more data before continuing.
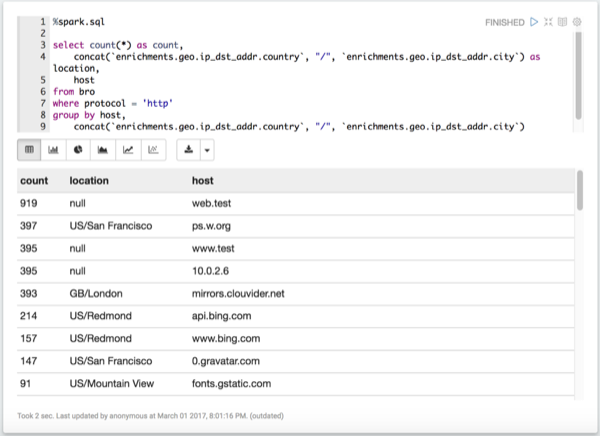
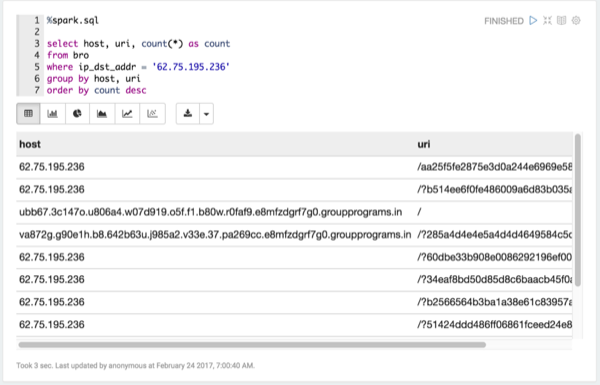
List the most active Bro hosts.
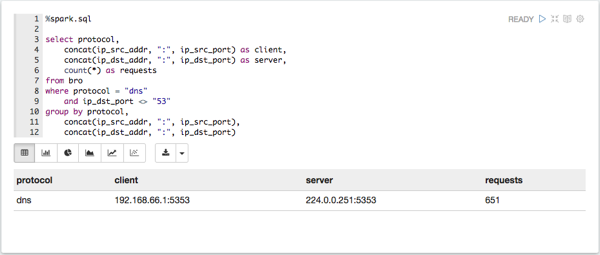
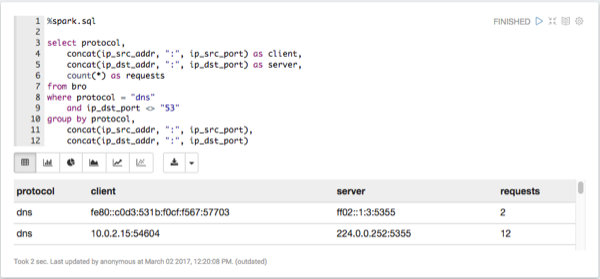
List any DNS servers running on non-standard ports.
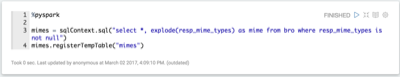
List any mime types that could be concerning.
Explode the HTTP records.
Each HTTP record can contain multiple mime types. These need to be 'exploded' to work with them properly.
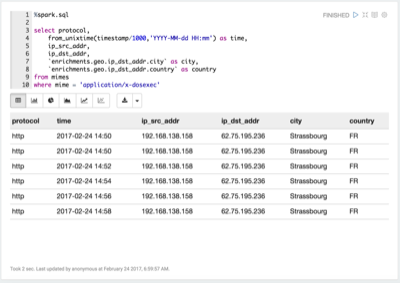
Determine where
application/x-dosexecoriginated.Take a look at the requests for
x-dosexc.Determine when the interactions with the suspicious host are occurring.