Using TLS wire encryption with DLM
DLM includes an optional transport level security (TLS) wire encryption feature. TLS (formerly SSL) provides in-flight encryption so that data is securely transferred between source and destination clusters. TLS wire encryption uses Knox proxied endpoints for HDP services accessed by the DLM engine within each cluster.
Using wire encryption in DLM-enabled clusters is optional. However, wire encryption must be configured the same within clusters paired in a source/destination relationship in DLM. That is, both clusters in a pairing must have intracluster encryption enabled using TLS or both must have TLS disabled.
- DLM Engine communications on the source are proxied through Knox using HTTPS.
- DLM Engine on the destination cluster communicates with the source cluster services (source DLM Engine, Ranger, and Hive) by proxying through Knox using HTTPS.
- The DLM Engine uses two-way SSL to authenticate token requests.
- DistCp on the destination uses SASL+QoP=privacy to communicate with the HDFS services on the source and destination clusters.
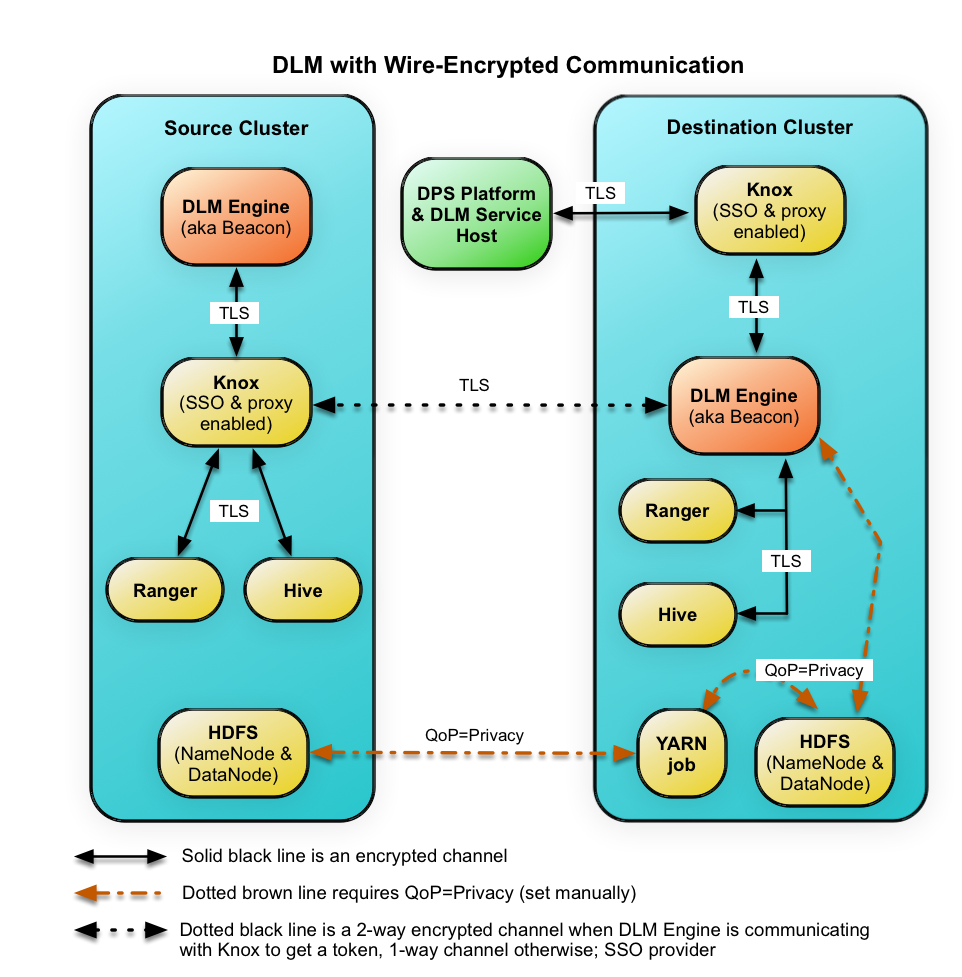
When wire encryption is enabled in the cluster, Knox proxying should be set up and enabled.

