Authentication with AWS
There are two ways for Cloudbreak to authenticate with AWS: be role-based or key-based.
After launching Cloudbreak on AWS, you are required to select one way for Cloudbreak to authenticate with your AWS account and create resources on your behalf: key-based or role-based. While key-based authentication simply uses your AWS access key and secret key, role-based authentication uses IAM roles.
Role-based authentication
If you are using role-based authentication for Cloudbreak on AWS, you will eventually create two IAM roles: one to grant Cloudbreak access to allow Cloudbreak to assume AWS roles (using the “AssumeRole” policy) and the second one to provide Cloudbreak with the capabilities required for cluster creation (using the “CbPolicy” policy).
The following diagram and table provide contextual information about the two roles required:
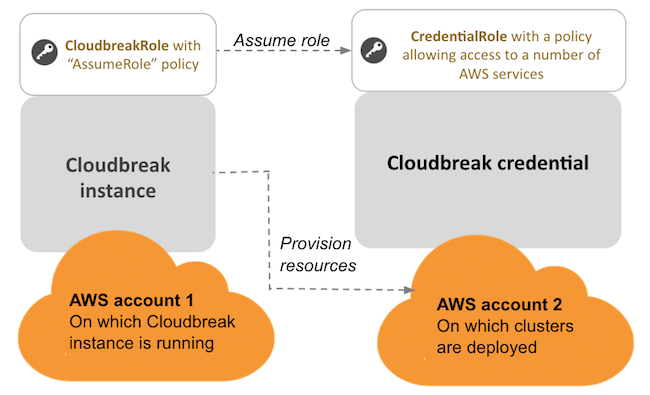
 | Note |
|---|---|
The AWS account 1 and AWS account 2 presented in the diagram can be the same account. |
| Role | Purpose | Overview of steps | Where to perform |
|---|---|---|---|
| CloudbreakRole | Allows Cloudbreak to assume other IAM roles - in this case Cloudbreak will assume the CredentialRole. |
|
|
| CredentialRole | Allows Cloudbreak to create AWS resources, such as VMs, required for clusters. |
|
|
 | Note |
|---|---|
These role and policy names are just examples. You may use different names when creating your resources. |
Alternatively, instead of attaching the “CloudbreakRole” role during the VM launch, you can assign the “CloudbreakRole” to an IAM user and then add the access and secret key of that user to your ‘Profile’.
Alternatively you can generate the “CredentialRole” role later once your Cloudbreak VM
is running by SSHing to the Cloudbreak VM and running the cbd aws
generate-role command. This command creates a role with the name
“cbreak-deployer” (equivalent to the “CredentialRole”). To customize the name of the
role, add export AWS_ROLE_NAME=my-cloudbreak-role-name (where
“my-cloudbreak-role-name” is your custom role name) as a new line to your Profile. If
you choose this option, you must make sure that the “CloudbreakRole” or the IAM user
have a permission not only to assume a role but also to create a role.

